We’re getting quite a few questions about how to set the admin password in OpenStack Windows instances, so let’s clarify the available options.
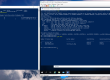
nova get-password
The secure and proper way to set passwords in OpenStack Windows instances is by letting Cloudbase-Init generate a random password and post it encrypted on the Nova metadata service. The password can then be retrieved with:
|
1 |
nova get-password <instance> [<ssh_private_key_path>] |
You need to boot your instance with a SSH keypair (exactly like you would do on Linux for SSH public key authentication). In this case the public key is used to encrypt the password before posting it to the Nova HTTP metadata service. This way nobody will be able to decrypt it without having the keypair’s private key.
This option is also well supported in Horizon, but not enabled by default. To enable it, just edit openstack_dashboard/local/local_settings.py and add:
|
1 |
OPENSTACK_ENABLE_PASSWORD_RETRIEVE = True |
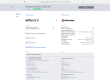
To retrieve the password in Horizon, select “RETRIEVE PASSWORD” from the instance dropdown menu:
Click “DECRYPT PASSWORD” (de decryption will occur in the browser, no data will be sent to the server) and retrieve your password:
nova boot –meta admin_pass
In case a password automatically generated is not suitable, there’s an option to provide a password via command line. This is NOT RECOMMENDED due to the security implications of sharing clear text passwords in the metadata content.
In this case the password is provided to the Nova instance via metadata service and assigned by Cloudbase-Init to the admin user:
|
1 |
nova boot --meta admin_pass="<password>" ... |
Given the previously mentioned security concerns this feature is disabled by default in Cloudbase-Init. In order to enable it inject_user_password must be set to true in the cloudbase-init.conf and cloudbase-init-unattend.conf config files:
|
1 |
inject_user_password = true |
Password change in userdata script
The userdata can contain any PowerShell content (note the starting #ps1 line to identify it as such), including commands for creating users or setting passwords, providing a much higher degree of flexibility. The same security concerns for clear text content apply as above.
The main limitation is that it does not work with Heat or other solutions that already employ the userdata content for other means.
Passwordless authentication
Nova allows X509 keypairs to support passwordless authentication for Windows. This is highly recommended as it does not require any password, similarly to SSH public key authentication on Linux. The limitations of this option is that it works only for remote PowerShell and WinRM and not for RDP.